Dear readers, With the launch of e-newsletter CUHK in Focus, CUHKUPDates has retired and this site will no longer be updated. To stay abreast of the University’s latest news, please go to https://focus.cuhk.edu.hk. Thank you.
The Devils are in the Clicks
Meng Wei on cyber security and click interception problems

Quick question: have you ever come across the following prompts or pop-up texts when browsing the Internet?
‘Congratulations! You are the 10,000th visitor to this site. Click here to claim your reward!’
‘We have detected a virus on your computer. Press OK button to begin the repair process.’
‘Want to have free donuts for the rest of your life? Click this link.’
If your answer is yes, you are definitely not alone.
Sometimes clever, often tempting, and always distracting, scammers have progressively made use of the net to bait computer users into clicking the contents they created, with the result that the latter might unwittingly share personal information or download malicious software into their computers.
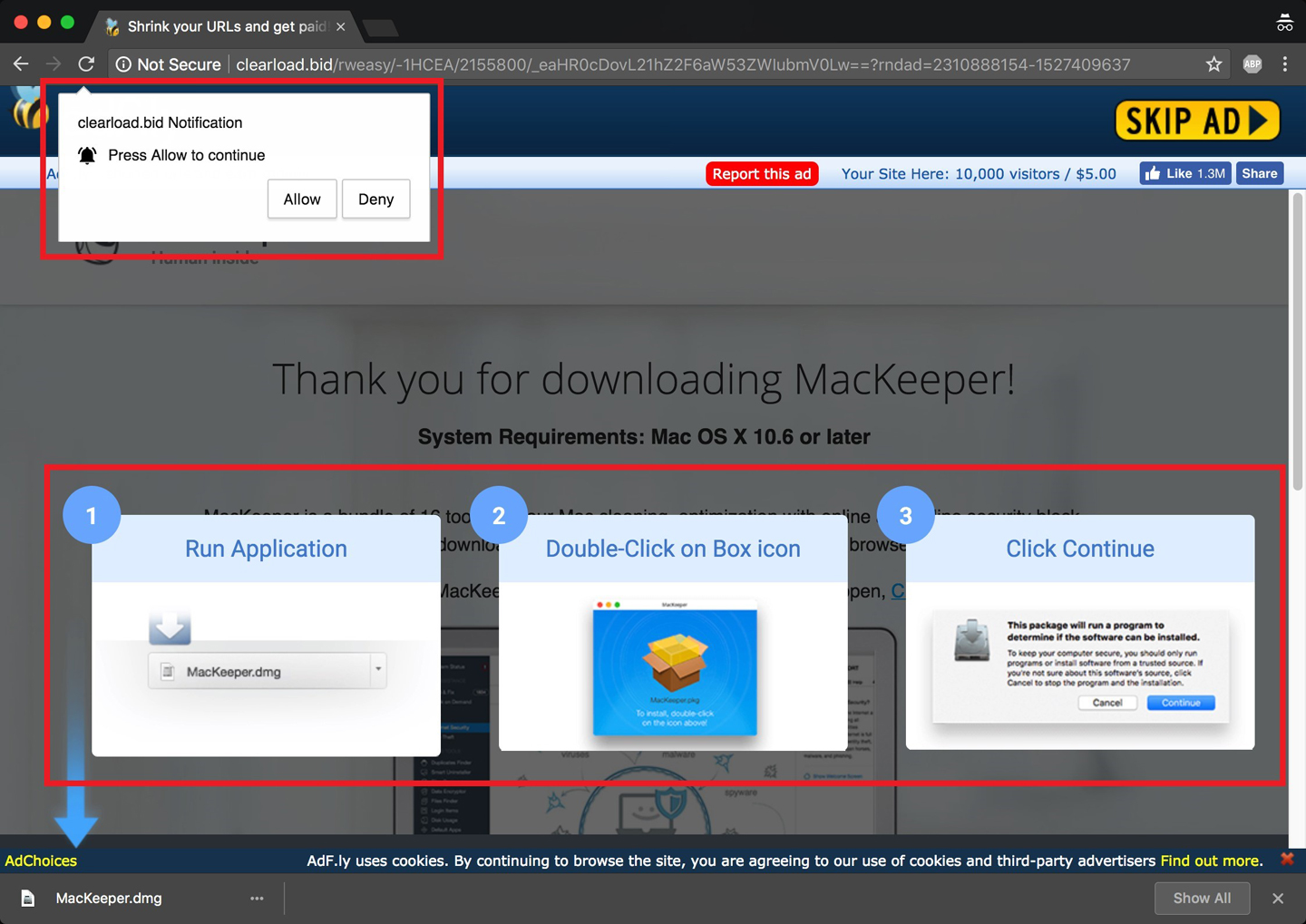
This hoax, commonly known as ‘clickbait’, is one of the ways for tricksters to find their preys online. Despite most users nowadays are alerted to these manipulations and are vigilant enough not to fall prey to deceptions, cyber fraudsters still got a few tricks up their sleeves.
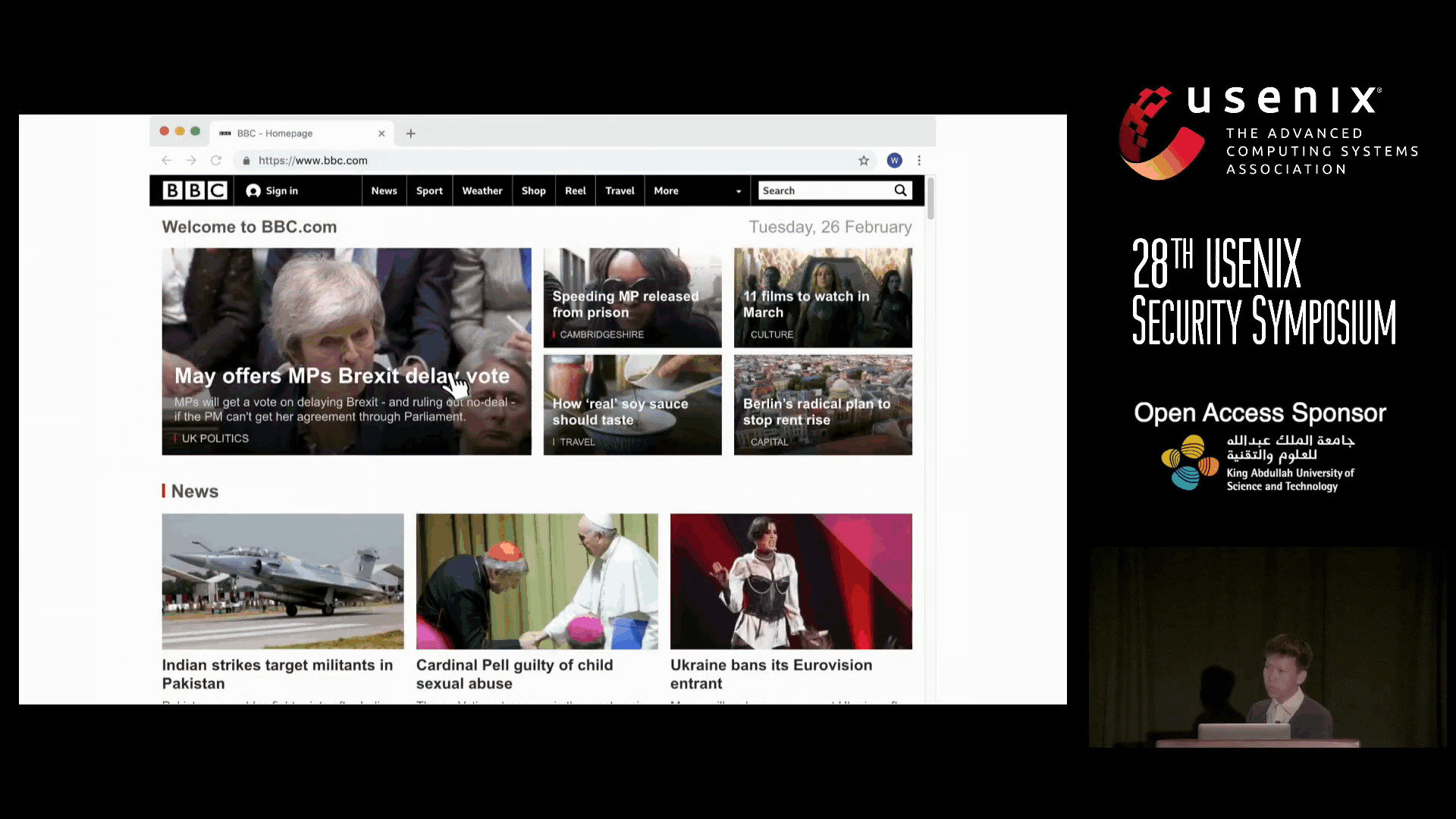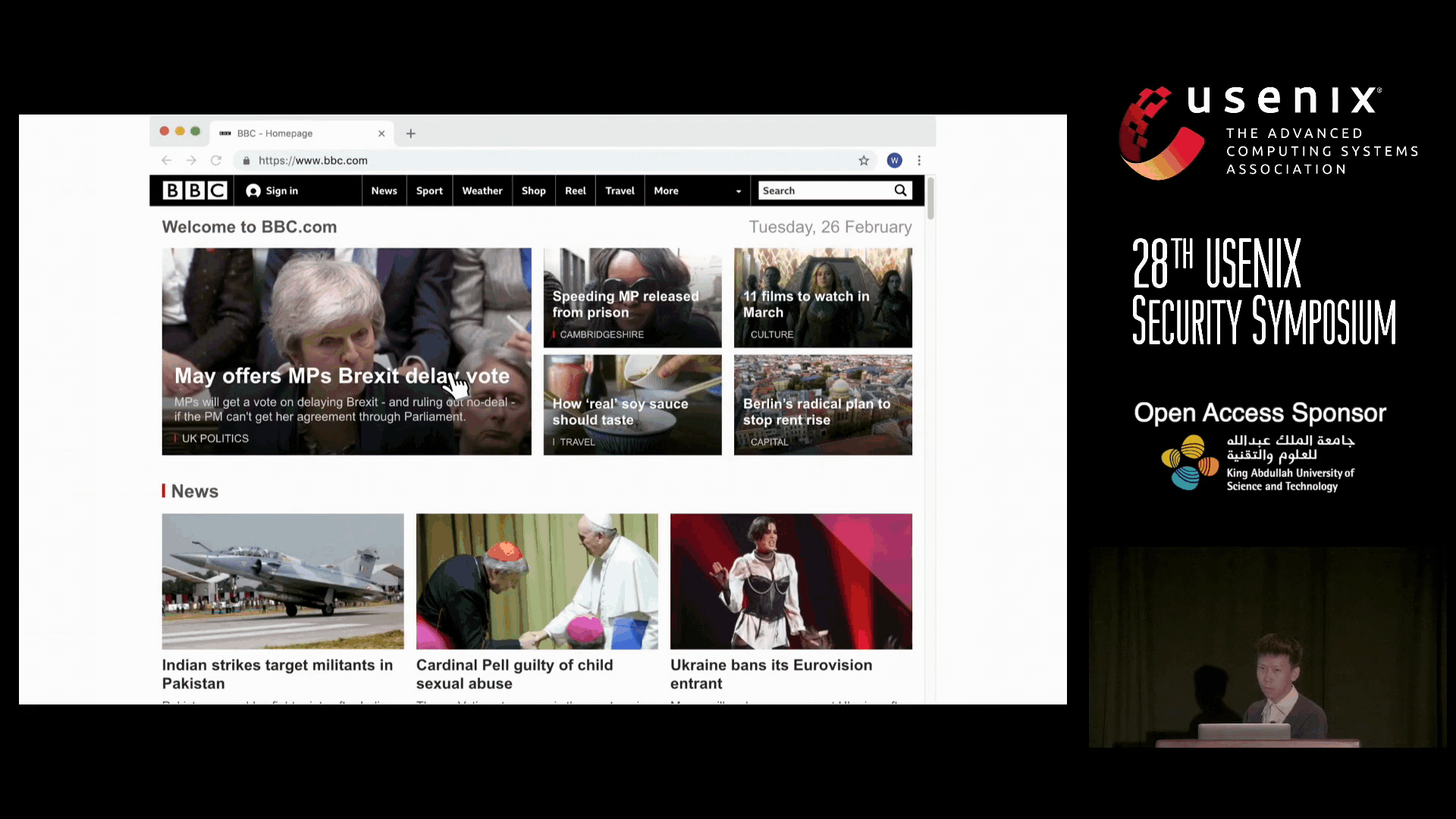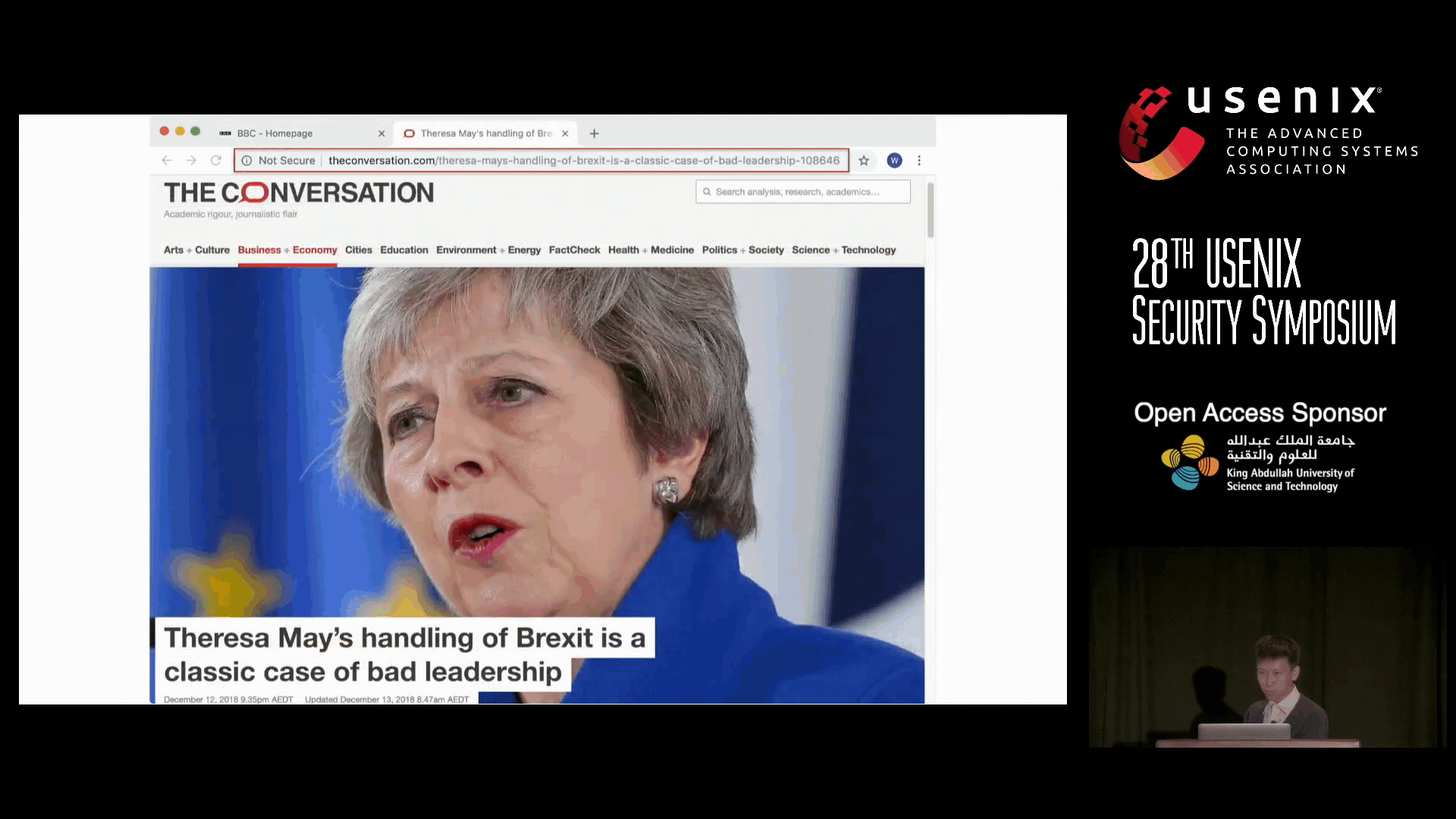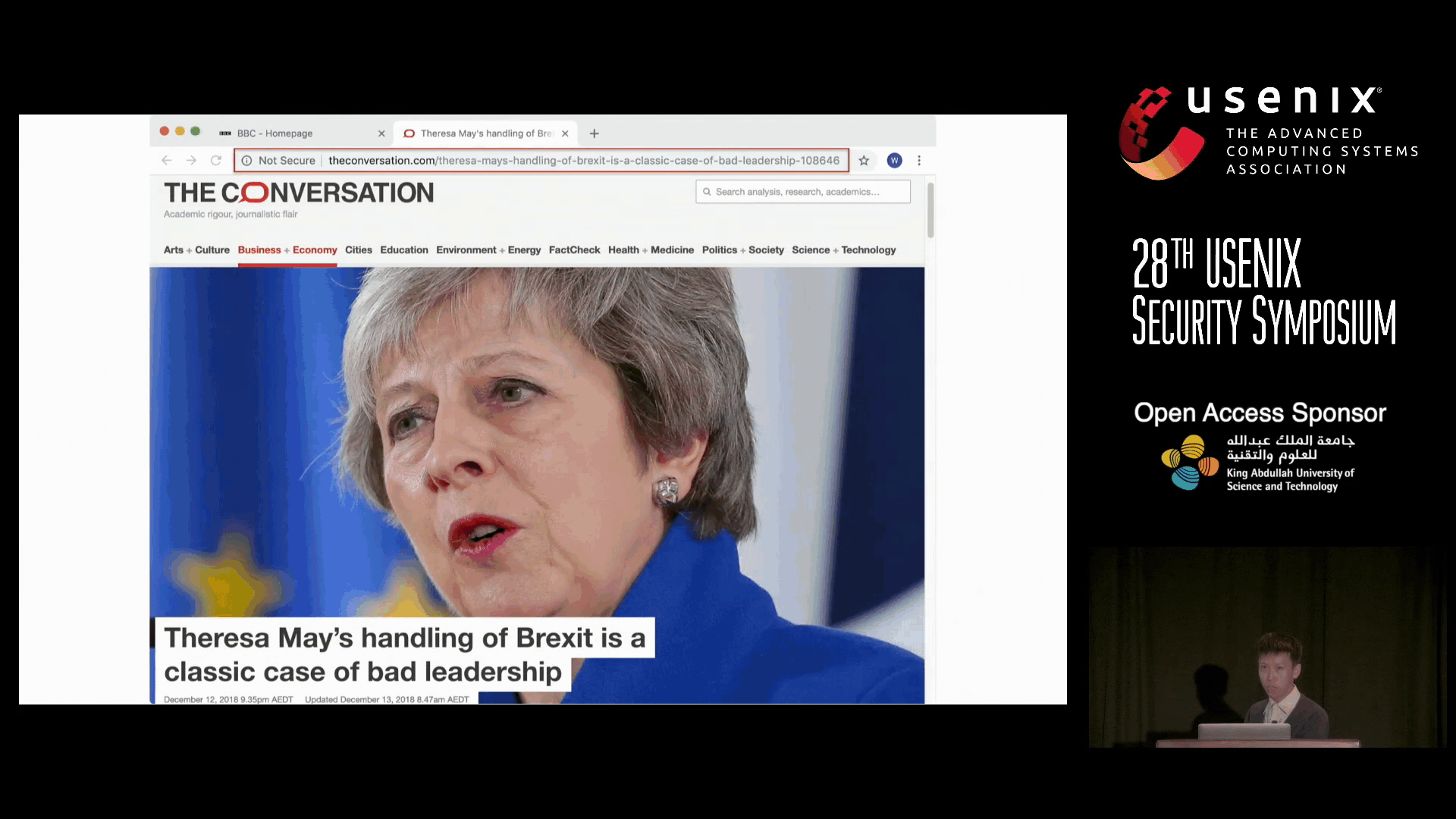
‘Picture this: you are a regular patron of BBC.com and, as usual, you are browsing its online website today. You make absolutely sure that you are accessing its official website. You see an interesting news article, click on it, and bam, you are now a potential victim of Adware or Trojan Horse,’ said Prof. Meng Wei of the Department of Computer Science and Engineering. ‘Yes, the browser still opens a page, but one that is malicious and not hosted on BBC.com at all.’
A learner, a thinker and a lover of science, Professor Meng has always been fascinated by the challenges posed by the virtual world and enjoys debunking its enigmas. Of all the problems he came across, he finds those relating to Internet security and browser privacy most captivating.
‘People have always thought that if they install a certain antivirus software or visit a webpage they have browsed before, they can avoid running into any Internet cyber-attacks. This is actually a big misconception,’ Professor Meng commented. ‘Take click interception—the practice of manoeuvring and redirecting legitimate users’ clicks by outside parties—for instance. There are tons of methods for cyber fraudsters to trick Internet users into clicking a webpage element, causing them to download malware, visit malicious website, leak personal information, and many more. Quite a lot of these methods, unfortunately, are not that easy to discern.’
Professor Meng has been studying the issues relating to privilege abuse on Internet browser back when he was a PhD student at Georgia Institute of Technology in 2016. Upon finishing his doctoral degree, he joined CUHK in 2017, continued his research on computer security design and privacy, and ultimately published his findings on the general techniques and theories behind click interception problems.
‘Despite the innumerable amount of click interception techniques, their modi operandi are actually more or less the same. It is about outsiders running their JavaScript codes inside content providers’ webpages and subsequently overwriting them in different ways in order to intercept clicks,’ he expounded. ‘Of all the techniques that we have found, a majority of them—roughly 86% to be exact—apply the method of “first-party hyperlink modification”, in which outsiders modify the codes in relation to electronic links and connect them to an external tampered webpage, usually one that is malicious and subjects users to potential cyber-attacks.’
Some of the techniques, however, can be very intricate and deceive even the most experienced users. ‘We have seen fabricated materials posted by fraudsters that look just as genuine as the content shown in bona fide webpages,’ he said. ‘Sometimes they are also able to create invisible icons to cover up the original content, directing users to a webpage other than the one that is intended to be visited or linked. These techniques are so subtle you can barely realize it is, in fact, a deception in disguise.’
To further take on the challenges that derived from click interceptions, Professor Meng joined forces with professors in Pennsylvania State University and Seoul National University and personnel from Microsoft Research to build ‘Observer’, a browser-based computer framework, to detect and analyze Internet users’ click-related behaviours.
‘Observer is basically a series of computer codes that can be implemented into a web browser and are able to observe the structures and dynamic behaviours of JavaScript, a programming language that allows users to make webpages,’ Professor Meng explained. ‘By comparing the JavaScript codes between websites that experience click interception problems and those that do not, we can see how attackers take control of a page by manipulating clicks, and in turn, figure out solutions to tackle the respective problems.’
Using Google Chrome browser as their base, Professor Meng and his team first visited a total of 250,000 websites and ran the Observer framework over two million ‘navigation Uniform Resource Locators’ (URLs), the first website that the browser would visit upon a user click. Upon sorting out the websites that experienced click manipulations, they then traced back the coding and compared the differences and similarities between all navigation URLs in click interception cases.
After many rounds of data compilation and careful analysis, Professor Meng made a thought-provoking discovery. ‘Surprisingly, about 36% of the click interception cases are related to online advertising,’ he remarked. ‘Upon further investigation, we discovered that some content providers, whether intentional or not, actually allow third parties to modulate user clicks in their webpages in return for money.’
According to Professor Meng, this phenomenon has much to do with the ‘pay-per-click’ billing model in online display advertising: content providers such as publishers are usually paid by advertisers when users click the advertisers’ ad in their webpages. Hence, in order to boost revenue and earn commission from participating advertisers, the most straightforward approach to generate users’ clicks is by forcing them to go through the ad before navigating to the original destination page.
‘Business is business, so content providers often do not care much about whether the advertisers are acting in good faith or not. This in turn gives fraudsters leeway to exploit the online platform to intercept clicks and trick users into visiting malicious webpages.’
Professor Meng had disseminated the above findings in the 28th USENIX Security Symposium, an open access media platform that allows researchers and scholars to share their latest discoveries in security and privacy of computer systems and networks to the world. His team has also released the source code of their framework publicly to help web browsers to detect probable click interceptions and alert users about malicious behaviours in webpages.
‘Our goal is to protect end users from visiting potentially attacker-controlled webpages and from being exposed to pernicious content on the Internet,’ he said.
Looking ahead, Professor Meng has a full schedule of work waiting for him and his team to accomplish. ‘Besides fine-tuning the accuracy of Observer and making it a real-time detection tool for Internet users, we are planning to study similar security matters in other mobile platforms, including cell phones and tablets, and also other security and privacy issues that pose serious threats to Internet users.’
Cyber security and public health are similar in many senses: we all have heard about the ways to protect ourselves amidst the COVID-19 pandemic, such as wearing a mask, washing our hands, practicing social distancing, and so on. The lesson we learnt here is crystal clear, that every one of us has a role to play in slowing, and eventually stopping, the virus’ propagation.
‘This is also the case in the world of technology—whether you like it or not, the problems relating to click interception are here to stay; of course, website owners should make sure that their web assets cannot be used to result in click interception attacks, but in case they do not or fail to do so, taking simple, common-sense security measures of your own volition can really protect yourself against cyber criminals and their attacks,’ said Professor Meng. ‘Remember, always update all of your softwares in a timely fashion and visit websites that are trustworthy. Never click anything that you do not know and be extra vigilant if you are asked to give out personal information or install unknown software. It is better to be safe than sorry.’
As ever, prevention is better than cure.
By ronaldluk@cuhkcontents
Photos by gloriang@cuhkimages